Cryptography and Elections: A Primer for Policymakers and Implementers

Cryptography is a branch of mathematics that deals with the encryption and decryption of information. It is used to protect sensitive information from unauthorized access, and it plays a vital role in the security of elections.
5 out of 5
| Language | : | English |
| File size | : | 276 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 5 pages |
| Lending | : | Enabled |
Cryptography can be used to protect the secrecy of votes, the integrity of the voting process, and the fairness of the election results. By using cryptography, election officials can ensure that only eligible voters can cast a ballot, that each voter can only cast one ballot, and that the votes are counted accurately.
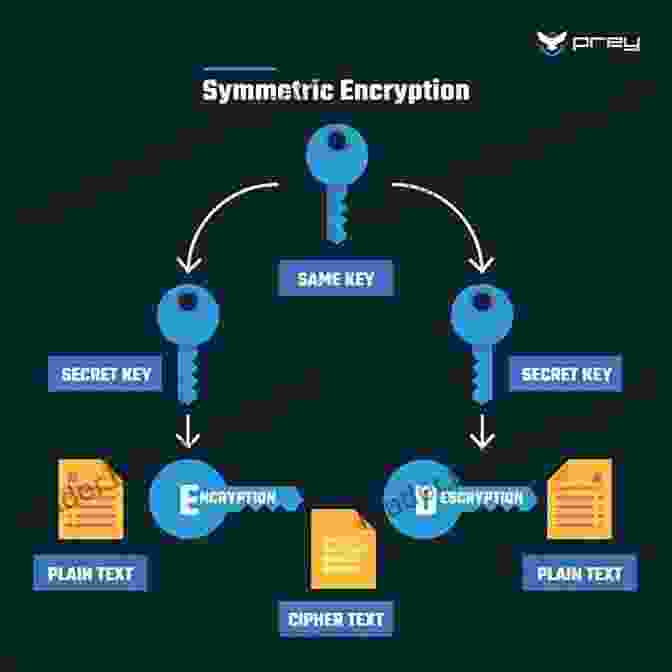
There are a number of different cryptographic algorithms that can be used in elections. The most common algorithm is the Advanced Encryption Standard (AES). AES is a symmetric-key algorithm, which means that the same key is used to encrypt and decrypt data.
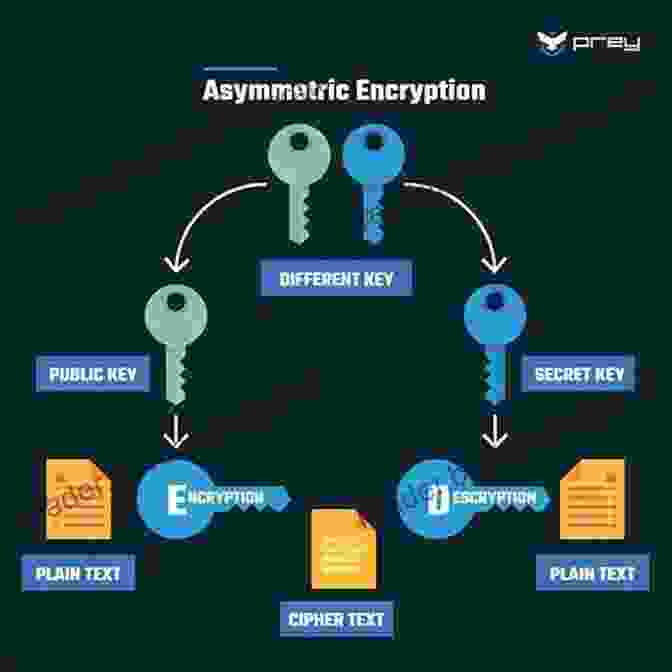
Other cryptographic algorithms that can be used in elections include the Rivest-Shamir-Adleman (RSA) algorithm, the Elliptic Curve Digital Signature Algorithm (ECDSA),and the SHA-256 hash function.
When designing and implementing an election system, it is important to consider the security considerations that must be taken into account. These considerations include:
- The confidentiality of the votes
- The integrity of the voting process
- The fairness of the election results
- The efficiency of the voting process
- The cost of the voting process
Cryptography can play a vital role in addressing these security considerations. By using cryptography, election officials can ensure that elections are secure, fair, and efficient.
The Benefits of Using Cryptography in Elections
There are a number of benefits to using cryptography in elections. These benefits include:
- Increased security: Cryptography can help to protect the secrecy of votes, the integrity of the voting process, and the fairness of the election results.
- Reduced costs: Cryptography can help to reduce the costs of elections by eliminating the need for paper ballots and other expensive voting equipment.
- Increased efficiency: Cryptography can help to increase the efficiency of elections by making it easier for voters to cast a ballot and for election officials to count the votes.
- Increased transparency: Cryptography can help to increase the transparency of elections by making it possible for voters to verify the integrity of the voting process.
The Challenges of Using Cryptography in Elections
There are also a number of challenges to using cryptography in elections. These challenges include:
- The complexity of cryptography: Cryptography is a complex subject, and it can be difficult for policymakers and implementers to understand how it works.
- The cost of cryptography: Cryptographic algorithms can be computationally expensive, and this can make it difficult to implement cryptography in large-scale elections.
- The security of cryptography: Cryptographic algorithms are not perfect, and it is possible for attackers to break them.
The Future of Cryptography in Elections
Despite the challenges, cryptography is playing an increasingly important role in elections. As the world becomes more digital, the need for secure and reliable voting systems is growing. Cryptography is one of the most powerful tools that we have to protect the integrity of elections.
In the future, we can expect to see even more use of cryptography in elections. Cryptographic algorithms are becoming more efficient and more secure, and the cost of implementing cryptography is decreasing. This makes it more feasible to use cryptography in large-scale elections.
As cryptography continues to evolve, we can expect to see new and innovative ways to use it to protect the integrity of elections. Cryptography is a vital tool for ensuring that elections are secure, fair, and efficient.
Cryptography is a powerful tool that can be used to protect the integrity of elections. By using cryptography, election officials can ensure that only eligible voters can cast a ballot, that each voter can only cast one ballot, and that the votes are counted accurately.
The use of cryptography in elections is still in its early stages, but it is rapidly becoming more widespread. As cryptographic algorithms become more efficient and more secure, and the cost of implementing cryptography decreases, we can expect to see even more use of cryptography in elections.
Cryptography is a vital tool for ensuring that elections are secure, fair, and efficient.
Image Alt Tags
5 out of 5
| Language | : | English |
| File size | : | 276 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 5 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Sam Subity
Sam Subity Nada Bakos
Nada Bakos M J Fievre
M J Fievre Sarah Winifred Searle
Sarah Winifred Searle Tara Teaspoon
Tara Teaspoon Michael Kimmelman
Michael Kimmelman Richard Monte
Richard Monte Laura Bellmont
Laura Bellmont Pete Cohen
Pete Cohen Lisa Edwards
Lisa Edwards Wolf Moon
Wolf Moon Michael Dante Dimartino
Michael Dante Dimartino Stan D Jensen
Stan D Jensen Luciano Simonelli
Luciano Simonelli Rosary O Neill
Rosary O Neill Leatrice Eiseman
Leatrice Eiseman Stewart Giles
Stewart Giles Kirsten Pai Buick
Kirsten Pai Buick Norihiro Yagi
Norihiro Yagi Kristina Cowan
Kristina Cowan
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Chuck MitchellFamous Annotated Story And Classic Illustrated: A Literary Gem for the Ages
Chuck MitchellFamous Annotated Story And Classic Illustrated: A Literary Gem for the Ages James GrayFollow ·13.9k
James GrayFollow ·13.9k Kelly BlairFollow ·4.8k
Kelly BlairFollow ·4.8k Milton BellFollow ·12.2k
Milton BellFollow ·12.2k Paulo CoelhoFollow ·7.8k
Paulo CoelhoFollow ·7.8k Howard BlairFollow ·17.9k
Howard BlairFollow ·17.9k Jermaine PowellFollow ·14.3k
Jermaine PowellFollow ·14.3k Chuck MitchellFollow ·4.4k
Chuck MitchellFollow ·4.4k Aldous HuxleyFollow ·17.8k
Aldous HuxleyFollow ·17.8k

 Liam Ward
Liam WardUnleash the Power of Goblin Slayer: Discover the Gripping...
Enter the Shadowy Realm of...

 Eli Brooks
Eli BrooksWalking the Territory: Your Essential Companion for...
Adventure Awaits! Prepare to immerse yourself...

 Floyd Richardson
Floyd RichardsonGoblin Slayer: A Gripping Light Novel Series That Will...
Step into the shadowy...

 Dennis Hayes
Dennis HayesFrom Strategy to ROI: The Ultimate Guide to Driving...
In the dynamic and competitive business...

 Edward Reed
Edward ReedUnveiling the Rich Tapestry of Tennis in Britain: A...
: Tennis - A British Love Affair Tennis, a...

 Michael Crichton
Michael CrichtonEscape into the Thrilling World of "Here and Now" by...
In the tapestry...
5 out of 5
| Language | : | English |
| File size | : | 276 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 5 pages |
| Lending | : | Enabled |